A truststore is a file that contains one or more public certificates, but no private keys.

A keystore is a file that contains one or more public certificates and one or more private keys. This is typically a “chain” where the keystore contains the root certificate authority (CA) certificate, the intermediate certificate authority (CA) certificate (issued by the root CA), and one or more server certificates (issued by the intermediate CA).

Let’s say you have a web server that produces HTTPS web pages, such as https://www.example.com. When a client submits a request to get a web page from your web server, a TLS handshake occurs, so that the packets exchanged between the client and server are encrypted. In this scenario, a keystore could be used. The keystore on the server would contain the public certificate and private key that will be used. A keystore is a file such as foo.p12 or bar.jks.
A keystore contains both public certificates and private keys
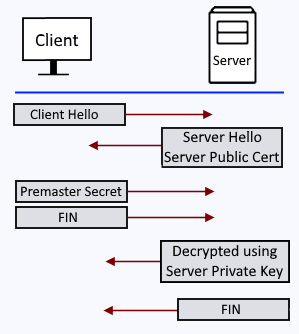
The TLS handshake look like this.
- The client sends a “Client Hello” packet to the server.
- The server sends a “Server Hello” packet to the client, which includes the public certificate in the keystore file (not the private key).
- The client validates the public certificate against it’s list of known, trusted certificate authorities, and then sends the server a premaster secret (random string of data). The premaster secret is encrypted with the public certificate. The server decrypts the premaster secret with the private key in the keystore.
- The client generates a session key and sends the server a FIN (finished) packet.
- The server generates a session key and sends the client a FIN (finished) packet.
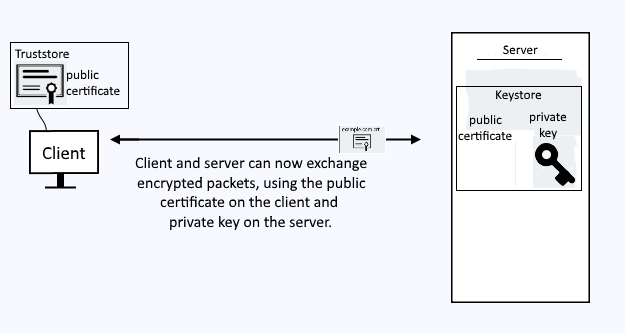
Let’s say you know you are going to be requesting a resource from a server often over a secured channel, such as HTTPS. Instead of going through the SSL handshake negotiation process to have the server provide you with the public certificate, you could store the servers public certificate in a truststore. Then, when you need to request a resource from the server, you will already have the certificate, so that you can present the certificate to the server and get on with the request. A truststore is a file, such as trust.p12.
A truststore contains public certificates. A truststore does not contain private keys.
The Java keytool command can be used to view, import, add, and remove public certificates and private keys from a keystore or truststore. In this example, the key.p12 keystore contains a public certificate called “default”. A private key doesn’t contain user specific data, such as an “alias” or “expiration date”, so the user specific data in the keystore represents the public certificates, not the private key.
~]# keytool -list -v -storetype PKCS12 -storepass changeit -keystore /path/to/key.p12
. . .
Alias: default
In this example, the trust.p12 truststore contains a public certificate called “example.com”.
~]# keytool -list -v -storetype PKCS12 -storepass changeit -keystore /path/to/trust.p12
. . .
Alias: example.com
《From: https://www.freekb.net/Article?id=1797》






没有回复内容